本机装的MySQL数据库密码忘记了,打开了Navicat连接过数据库,不过密码是加密的,怎么办呢?今天给大家分享如何查看Navicat加密的数据库密码,感兴趣的朋友一起看看吧。
查看Navicat加密的数据库密码
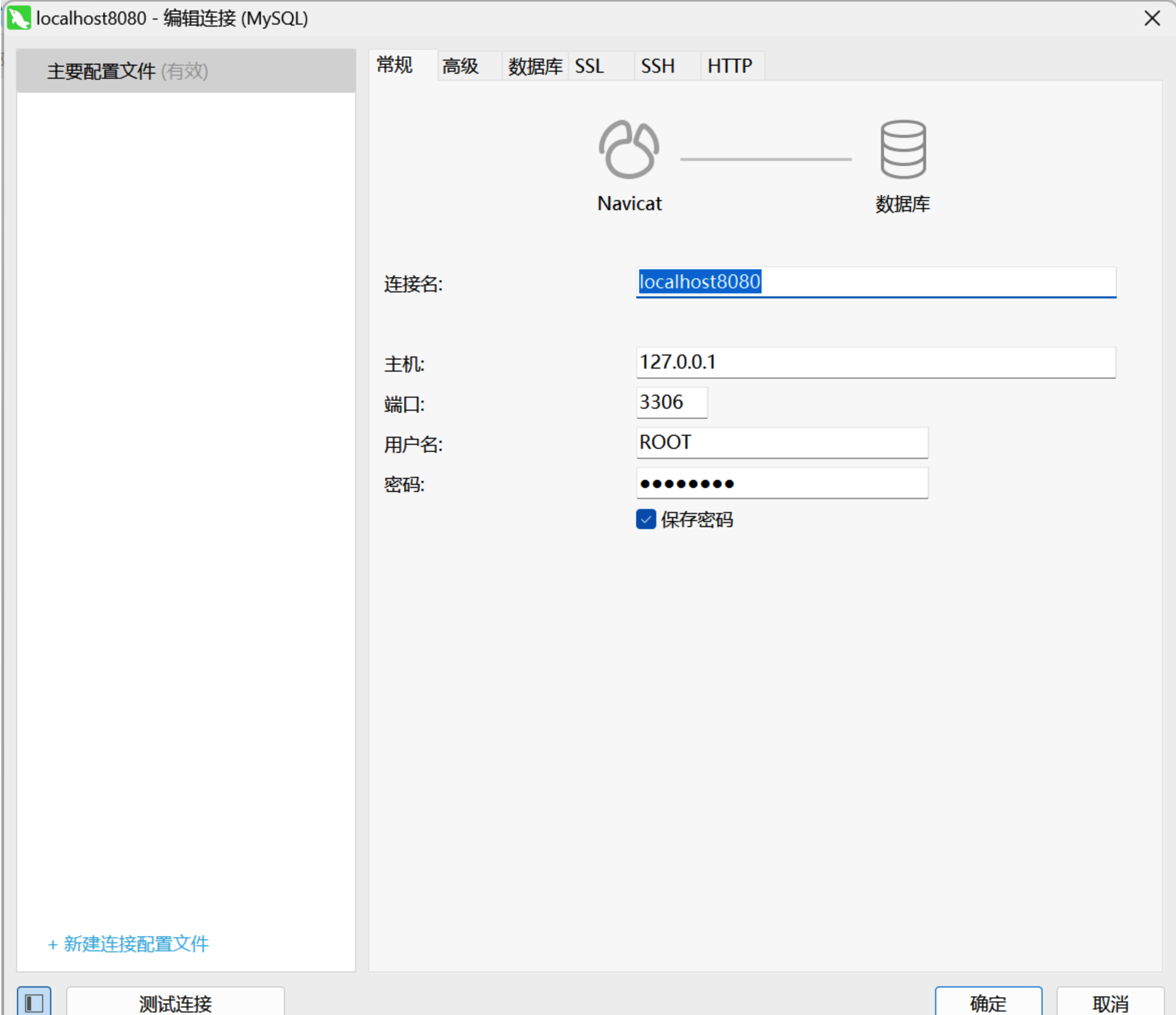
通过导出连接信息
点击navicat左上角导出连接信息 然后选择你要查看密码的数据库信息勾选导出密码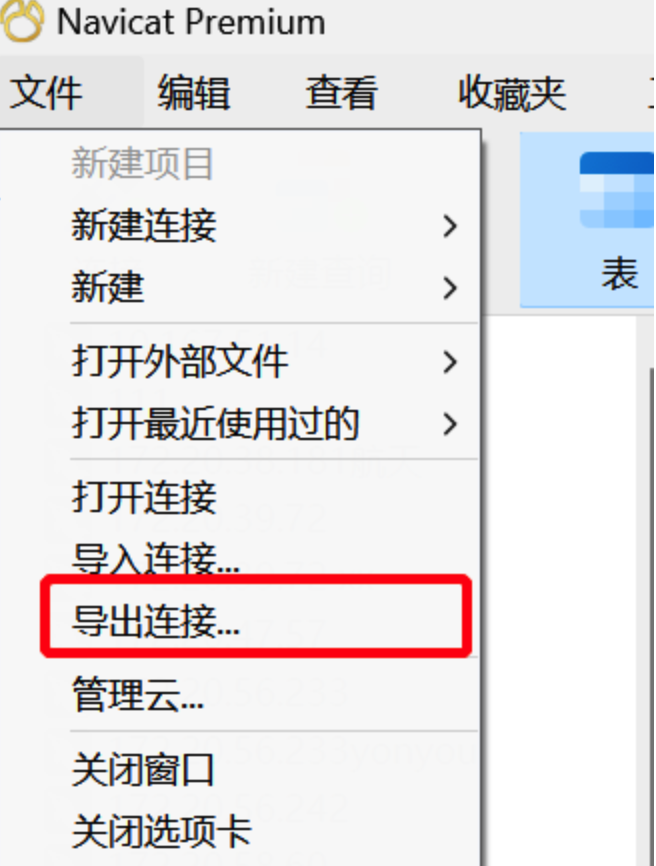
会导出一个.ncx文件 通过记事本打开 然后找到PassWord的加密密码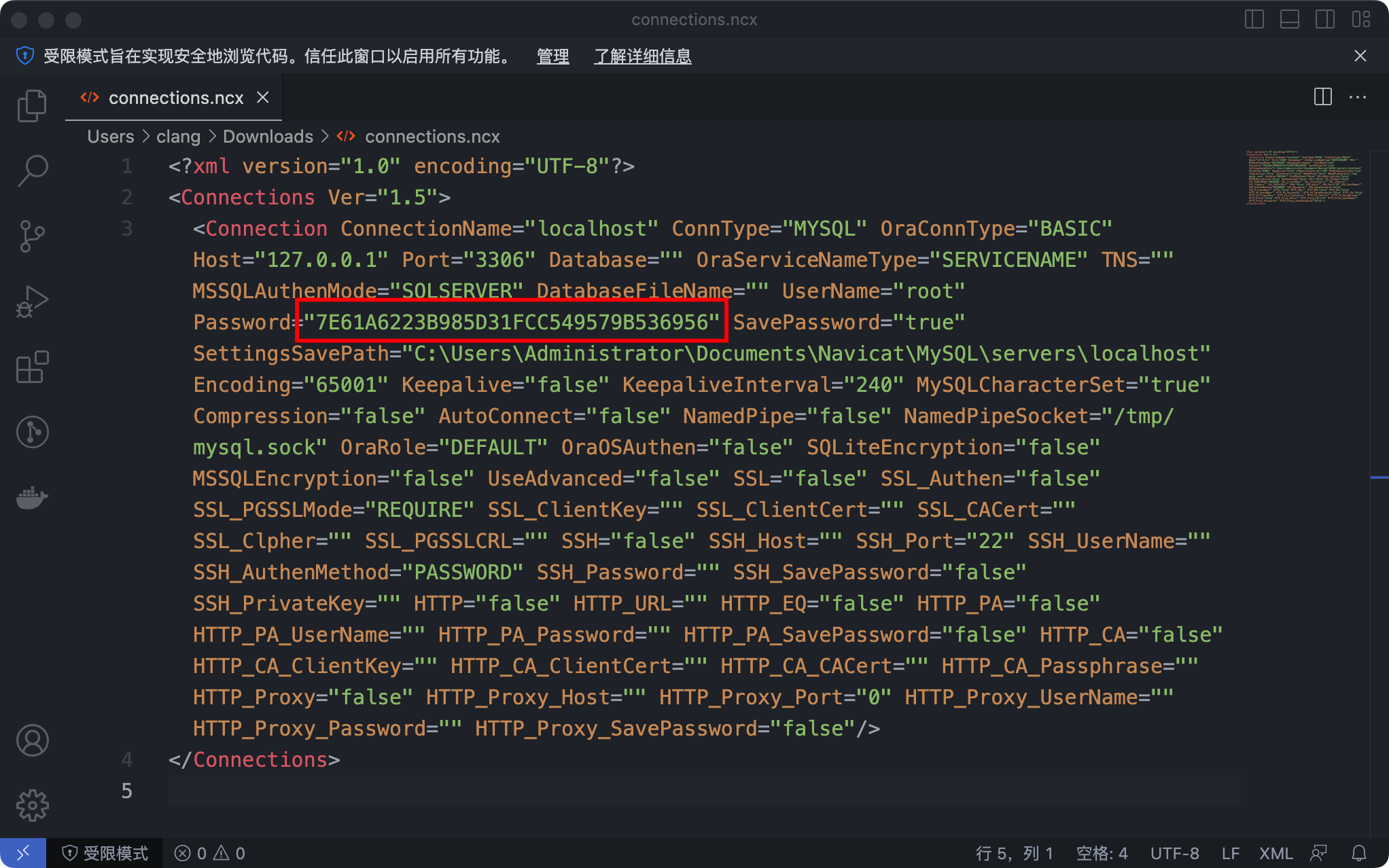
将Password引号后面的加密密钥7E61A6223B985D31FCC549579B536956复制出来
打开PHP在线运行工具,粘贴解密代码
- 工具地址:https://toolin.cn/run-php7
- 复制解密代码到工具中
<?php
class NavicatPassword
{
protected $version = 0;
protected $aesKey = 'libcckeylibcckey';
protected $aesIv = 'libcciv libcciv ';
protected $blowString = '3DC5CA39';
protected $blowKey = null;
protected $blowIv = null;
public function __construct($version = 12)
{
$this->version = $version;
$this->blowKey = sha1('3DC5CA39', true);
$this->blowIv = hex2bin('d9c7c3c8870d64bd');
}
public function encrypt($string)
{
$result = FALSE;
switch ($this->version) {
case 11:
$result = $this->encryptEleven($string);
break;
case 12:
$result = $this->encryptTwelve($string);
break;
default:
break;
}
return $result;
}
protected function encryptEleven($string)
{
$round = intval(floor(strlen($string) / 8));
$leftLength = strlen($string) % 8;
$result = '';
$currentVector = $this->blowIv;
for ($i = 0; $i < $round; $i++) {
$temp = $this->encryptBlock($this->xorBytes(substr($string, 8 * $i, 8), $currentVector));
$currentVector = $this->xorBytes($currentVector, $temp);
$result .= $temp;
}
if ($leftLength) {
$currentVector = $this->encryptBlock($currentVector);
$result .= $this->xorBytes(substr($string, 8 * $i, $leftLength), $currentVector);
}
return strtoupper(bin2hex($result));
}
protected function encryptBlock($block)
{
return openssl_encrypt($block, 'BF-ECB', $this->blowKey, OPENSSL_RAW_DATA|OPENSSL_NO_PADDING);
}
protected function decryptBlock($block)
{
return openssl_decrypt($block, 'BF-ECB', $this->blowKey, OPENSSL_RAW_DATA|OPENSSL_NO_PADDING);
}
protected function xorBytes($str1, $str2)
{
$result = '';
for ($i = 0; $i < strlen($str1); $i++) {
$result .= chr(ord($str1[$i]) ^ ord($str2[$i]));
}
return $result;
}
protected function encryptTwelve($string)
{
$result = openssl_encrypt($string, 'AES-128-CBC', $this->aesKey, OPENSSL_RAW_DATA, $this->aesIv);
return strtoupper(bin2hex($result));
}
public function decrypt($string)
{
$result = FALSE;
switch ($this->version) {
case 11:
$result = $this->decryptEleven($string);
break;
case 12:
$result = $this->decryptTwelve($string);
break;
default:
break;
}
return $result;
}
protected function decryptEleven($upperString)
{
$string = hex2bin(strtolower($upperString));
$round = intval(floor(strlen($string) / 8));
$leftLength = strlen($string) % 8;
$result = '';
$currentVector = $this->blowIv;
for ($i = 0; $i < $round; $i++) {
$encryptedBlock = substr($string, 8 * $i, 8);
$temp = $this->xorBytes($this->decryptBlock($encryptedBlock), $currentVector);
$currentVector = $this->xorBytes($currentVector, $encryptedBlock);
$result .= $temp;
}
if ($leftLength) {
$currentVector = $this->encryptBlock($currentVector);
$result .= $this->xorBytes(substr($string, 8 * $i, $leftLength), $currentVector);
}
return $result;
}
protected function decryptTwelve($upperString)
{
$string = hex2bin(strtolower($upperString));
return openssl_decrypt($string, 'AES-128-CBC', $this->aesKey, OPENSSL_RAW_DATA, $this->aesIv);
}
};
//需要指定版本两种,11或12
//$navicatPassword = new NavicatPassword(11);
$navicatPassword = new NavicatPassword(12);
//解密
//$decode = $navicatPassword->decrypt('15057D7BA390');
$decode = $navicatPassword->decrypt('7E61A6223B985D31FCC549579B536956'); // 替换成上一步的数据数值
echo $decode."\n";
?>修改倒数第三行NavicatPassword的版本值
点击执行,右侧得到解密后的密码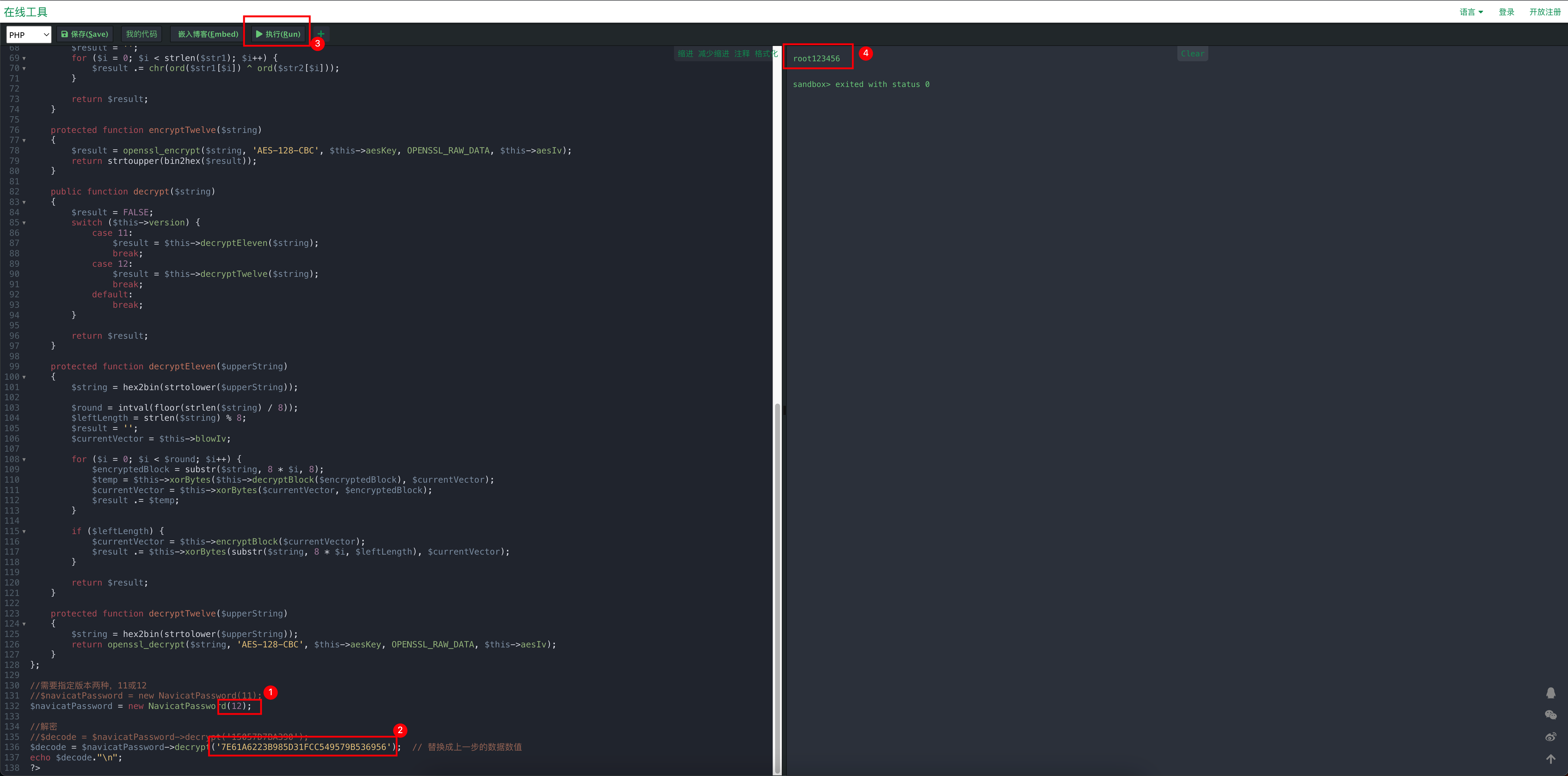
对应的Python代码
需要安装 PyCryptodome 库来提供加密算法支持:
pip install pycryptodomenavicat_password.py代码
import hashlib
import binascii
import argparse
from Crypto.Cipher import AES, Blowfish
from Crypto.Util.Padding import pad, unpad
class NavicatPassword:
def __init__(self, version=12):
self.version = version
self.aes_key = b'libcckeylibcckey' # 16字节
self.aes_iv = b'libcciv libcciv ' # 16字节
self.blow_string = '3DC5CA39'
# 计算Blowfish的密钥和IV
self.blow_key = hashlib.sha1(self.blow_string.encode()).digest()
self.blow_iv = binascii.unhexlify('d9c7c3c8870d64bd') # 8字节
def encrypt(self, string):
if self.version == 11:
return self.encrypt_eleven(string)
elif self.version == 12:
return self.encrypt_twelve(string)
return None
def decrypt(self, string):
if self.version == 11:
return self.decrypt_eleven(string)
elif self.version == 12:
return self.decrypt_twelve(string)
return None
def encrypt_eleven(self, string):
str_bytes = string.encode('utf-8')
length = len(str_bytes)
round_num = length // 8
left_length = length % 8
result = b''
current_vector = self.blow_iv
# 处理完整的8字节块
for i in range(round_num):
block = str_bytes[i*8 : (i+1)*8]
xor_block = self.xor_bytes(block, current_vector)
encrypted_block = self.encrypt_block(xor_block)
current_vector = self.xor_bytes(current_vector, encrypted_block)
result += encrypted_block
# 处理剩余字节
if left_length > 0:
current_vector = self.encrypt_block(current_vector)
block = str_bytes[round_num*8 :]
xor_block = self.xor_bytes(block, current_vector[:left_length])
result += xor_block
return binascii.hexlify(result).decode().upper()
def decrypt_eleven(self, upper_string):
string = binascii.unhexlify(upper_string.lower())
length = len(string)
round_num = length // 8
left_length = length % 8
result = b''
current_vector = self.blow_iv
# 处理完整的8字节块
for i in range(round_num):
encrypted_block = string[i*8 : (i+1)*8]
decrypted_block = self.decrypt_block(encrypted_block)
xor_block = self.xor_bytes(decrypted_block, current_vector)
current_vector = self.xor_bytes(current_vector, encrypted_block)
result += xor_block
# 处理剩余字节
if left_length > 0:
current_vector = self.encrypt_block(current_vector)
block = string[round_num*8 :]
xor_block = self.xor_bytes(block, current_vector[:left_length])
result += xor_block
return result.decode('utf-8', errors='replace')
def encrypt_twelve(self, string):
cipher = AES.new(self.aes_key, AES.MODE_CBC, self.aes_iv)
padded_data = pad(string.encode('utf-8'), AES.block_size)
encrypted = cipher.encrypt(padded_data)
return binascii.hexlify(encrypted).decode().upper()
def decrypt_twelve(self, upper_string):
encrypted_data = binascii.unhexlify(upper_string.lower())
cipher = AES.new(self.aes_key, AES.MODE_CBC, self.aes_iv)
decrypted_data = unpad(cipher.decrypt(encrypted_data), AES.block_size)
return decrypted_data.decode('utf-8', errors='replace')
def encrypt_block(self, block):
# Blowfish-ECB加密,需要8字节对齐
cipher = Blowfish.new(self.blow_key, Blowfish.MODE_ECB)
# 填充到8字节的倍数
pad_length = (8 - len(block) % 8) % 8
padded_block = block + b'\x00' * pad_length
return cipher.encrypt(padded_block)[:len(block)]
def decrypt_block(self, block):
# Blowfish-ECB解密,使用自定义填充处理
cipher = Blowfish.new(self.blow_key, Blowfish.MODE_ECB)
decrypted = cipher.decrypt(block)
# 移除填充(只移除末尾的空字节填充)
while decrypted and decrypted[-1] == 0x00:
decrypted = decrypted[:-1]
return decrypted
@staticmethod
def xor_bytes(str1, str2):
# 对两个字节串进行XOR操作
return bytes(a ^ b for a, b in zip(str1, str2))
# 使用示例
if __name__ == "__main__":
# 设置命令行参数解析
parser = argparse.ArgumentParser(description='Navicat密码解密工具')
parser.add_argument('-v', '--version', type=int, choices=[11, 12],
default=12, help='Navicat版本号,11或12,默认12')
parser.add_argument('-p', '--password', required=True,
help='需要解密的密码字符串')
parser.add_argument('-e', '--encrypt', action='store_true',
help='执行加密操作,默认是解密')
args = parser.parse_args()
# 创建实例
np = NavicatPassword(args.version)
# 执行操作
if args.encrypt:
result = np.encrypt(args.password)
print(f"加密结果: {result}")
else:
result = np.decrypt(args.password)
print(f"解密结果: {result}")
使用方法:
解密操作(默认)
python navicat_password.py -v 12 -p "7E61A6223B985D31FCC549579B536956"加密操作:
python navicat_password.py -v 11 -p "mypassword" -e参数说明:
-v 或 --version:指定 Navicat 版本号,只能是 11 或 12,默认 12
-p 或 --password:需要处理的密码字符串(必需参数)
-e 或 --encrypt:可选参数,如果指定则执行加密操作,默认是解密
 ╃苍狼山庄╃
╃苍狼山庄╃